This documentation is for Stably Classic. For the new Stably Web Editor, see Stably Web Editor.
Overview
Many applications use bot detection services to protect against automated attacks. However, these same systems can interfere with legitimate automated testing. This guide covers how to configure Stably to work with common bot detection systems.Cloudflare Bot Detection
If you see a Cloudflare bot detection page in your test failures, you likely have Cloudflare Bot Detection enabled.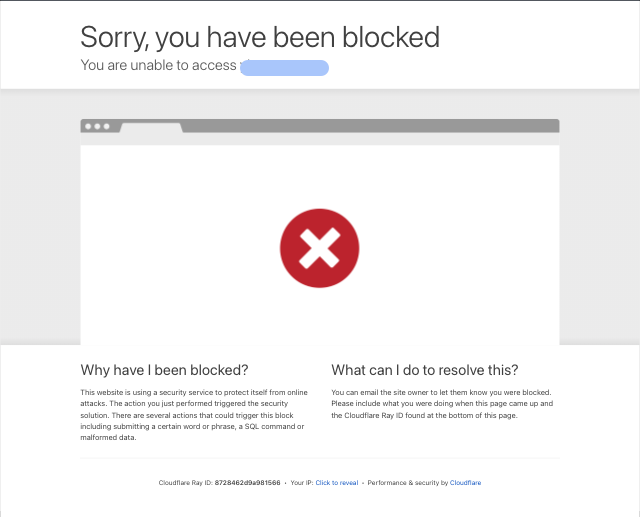
Cloudflare Access Users
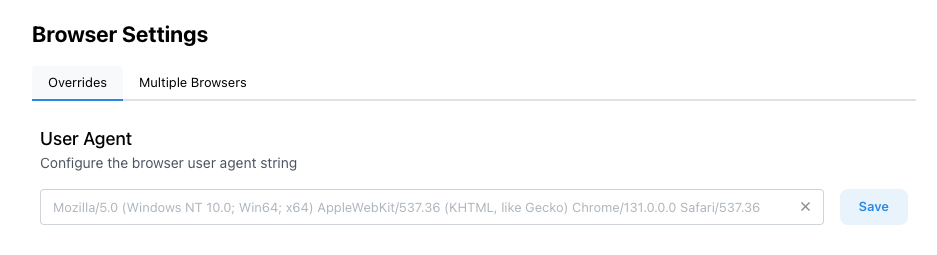
You can allowlist Stably’s User-Agent in your Cloudflare settings:- Navigate to Browser Settings in your Stably workspace
- Configure User-Agent to use a standard browser user agent instead of the default Stably identifier
- Update Cloudflare Settings to allowlist the configured user agent
Cloudflare Zero Trust Users
In Zero Trust environments, each action initiated by Stably needs to contain a service token:Generate Service Token
Create a service token in your Cloudflare console following the Cloudflare documentation
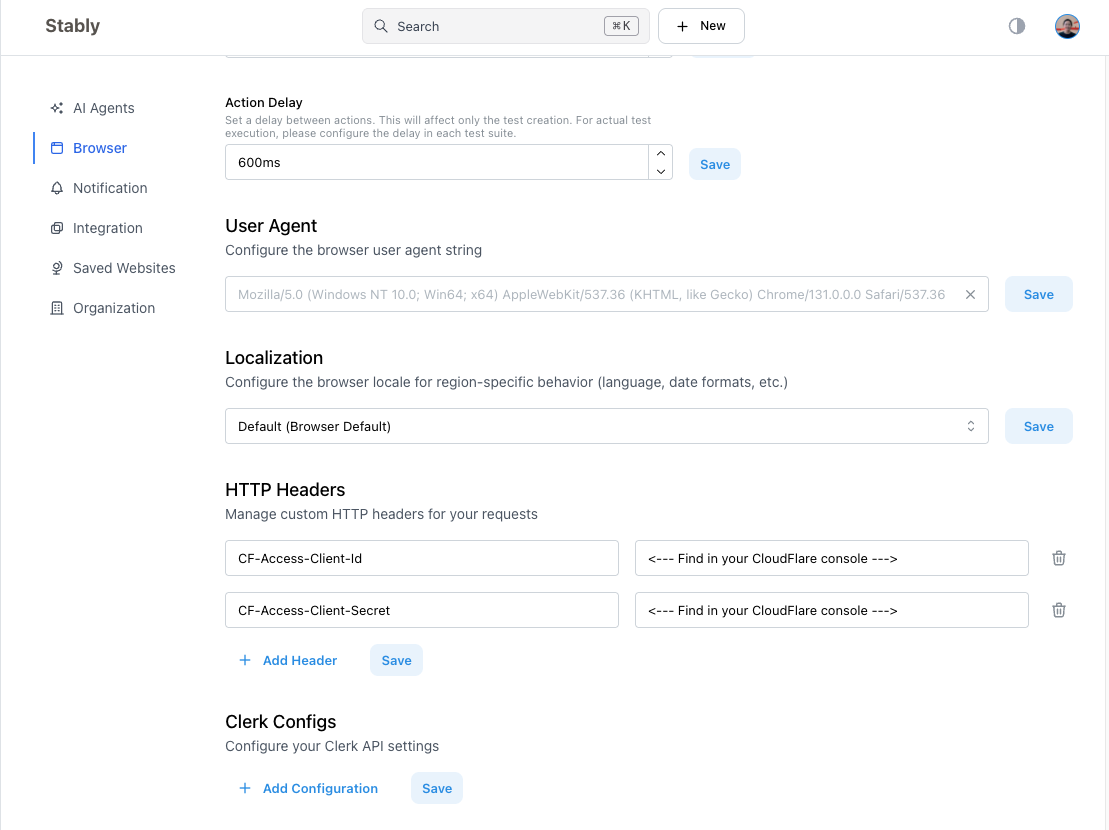
Add to HTTP Headers
Navigate to Browser Settings in Stably and add the service token to the HTTP Headers field
Clerk Bot Detection
If you encounter Clerk bot detection pages during test execution, you have Clerk Bot Detection enabled in your application.Solution 1: Disable Clerk Bot Detection on Staging
Recommended approach for staging environments:- Clerk doesn’t provide granular User-Agent allowlisting
- The most effective solution is to disable Clerk Bot Detection in your staging environment
- This allows automated testing while maintaining production security
Solution 2: Session Token API Integration
For production testing or when bot detection must remain enabled: Create an API endpoint that generates session tokens for Stably. This approach uses Clerk’s testing framework as described in their testing documentation.Implementation Example
Configuration Steps
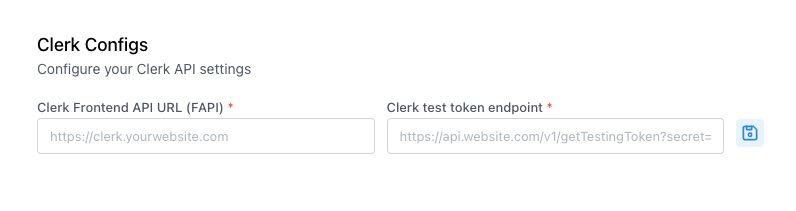
Configure in Browser Settings
Add the API endpoint URL in your Stably Browser Settings under Clerk Configurations
IP Allowlisting
For applications with strict bot detection that can’t be bypassed through user agent or header configuration, IP allowlisting provides a reliable solution.When to Use IP Allowlisting
IP allowlisting is effective when:- Bot detection systems are too aggressive to bypass with configuration changes
- You need guaranteed test execution without detection interference
- Your security policies allow IP-based exceptions for testing
- Other methods (user agent, headers, tokens) have proven insufficient
Implementation Steps
Obtain Stably IP Addresses
Contact Stably support to get the current list of IP addresses used for test execution. These IPs may change periodically, so ensure you have the most recent list.
Configure Your Security System
Add Stably’s IP addresses to your bot detection allowlist:
- Cloudflare: Add IPs to IP Access Rules or WAF allowlist
- Custom Security: Configure your security system to bypass bot detection for Stably IPs
- Load Balancer: Update load balancer rules to allow Stably traffic
Environment-Specific Configuration
Consider different approaches for different environments:
- Staging: Full IP allowlisting for comprehensive testing
- Production: Restricted allowlisting with monitoring
- Development: Flexible allowlisting for rapid iteration
Configuration Examples
Cloudflare IP Access Rules
WAF Rule Example
Considerations and Limitations
Security Implications:- IP allowlisting reduces security for allowlisted addresses
- Regularly review and update the allowlisted IP ranges
- Monitor traffic from allowlisted IPs for any suspicious activity
- Stably IP addresses may change with infrastructure updates
- Set up monitoring to detect when allowlisted IPs become inactive
- Establish a process for updating IP allowlists when Stably provides new ranges
- Ensure your CDN/security provider supports IP allowlisting
- Verify that allowlisting works across all geographic regions where tests run
- Test failover scenarios to ensure continued access during IP changes
General Bot Detection Best Practices
User Agent Configuration
- Use Standard User Agents: Configure a standard browser user agent instead of the default Stably identifier
- Rotate User Agents: Consider rotating between different standard user agents
- Environment-Specific: Use different user agents for different testing environments
HTTP Headers
Common headers that help bypass bot detection:Accept: Standard browser accept headersAccept-Language: Language preferencesAccept-Encoding: Compression preferencesReferer: Appropriate referer headers for navigation flows
Testing Strategy
- Start with Staging: Always test bot detection configurations in staging environments first
- Monitor Failures: Watch for bot detection patterns in test failures
- Gradual Implementation: Implement bypasses incrementally to identify the minimal required configuration
- Environment Separation: Use different configurations for different environments
Troubleshooting
Common Issues
Tests failing with bot detection pages:- Verify user agent configuration
- Check HTTP headers are properly set
- Ensure service tokens are valid and not expired
- Review rate limiting settings
- Consider adding delays between actions
- Check for IP-based restrictions
- Verify settings are saved in Browser Settings
- Check that configurations are applied to the correct environment
- Restart test execution after configuration changes
Getting Help
If you continue to experience bot detection issues:- Document the Detection: Capture screenshots of bot detection pages
- Gather Configuration: Note your current user agent and header settings
- Contact Support: Reach out with your configuration details and error patterns
Bot detection systems evolve frequently. Keep your anti-bot configurations updated and monitor test results for new detection patterns.